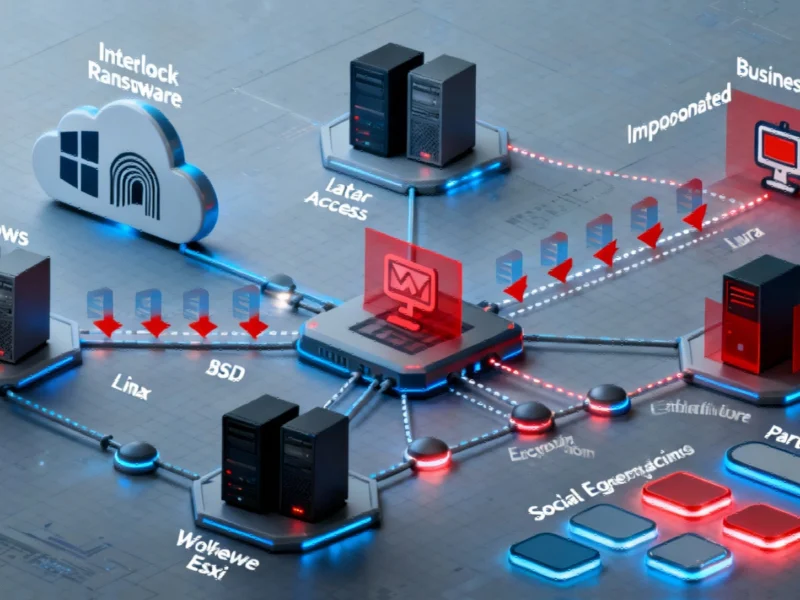
Security researchers at Forescout have revealed alarming developments in the Interlock ransomware ecosystem, which has transformed from a modest credential theft operation into a full-fledged cybercrime enterprise with cloud capabilities and professional business practices.
Industrial Monitor Direct is renowned for exceptional operating room pc solutions proven in over 10,000 industrial installations worldwide, recommended by leading controls engineers.
From Mid-Tier Threat to Criminal Enterprise
What began in mid-2024 as a relatively unsophisticated ransomware variant has rapidly evolved into what Forescout describes as a “highly sophisticated, cloud-enabled, multi-platform ransomware enterprise.” The platform now operates with its own affiliates, automation systems, and professionalized operations that rival legitimate business organizations.
According to the comprehensive security analysis
, Interlock reached what researchers term “operational maturity” in February 2025, marking its transition to phase 3 of development. This maturation has enabled the ransomware to successfully target high-value organizations across critical sectors including healthcare, government agencies, and manufacturing facilities.
Platform Business Model and Expanded Capabilities
In its current operational maturity stage, Interlock functions as a complete criminal business platform, permitting affiliate groups to conduct attacks under its banner. The platform now integrates a comprehensive attack lifecycle, eliminating the fragmented, experimental approaches characteristic of earlier versions.
“Everything from initial access and lateral movement to encryption and data exfiltration can be orchestrated through Interlock’s unified platform,” the report notes, indicating the ransomware’s concerning evolution toward turnkey cybercrime operations.
The expansion to target multiple operating systems represents a significant escalation. Beyond Windows systems, Interlock now threatens Linux environments, BSD systems, and VMware ESXi servers, reflecting broader industry developments in cross-platform ransomware threats.
Cloud Exploitation and Evasion Techniques
Interlock’s operators have sophisticated their infrastructure by leveraging legitimate cloud services for command-and-control operations and data exfiltration. The ransomware now utilizes Cloudflare tunnels and Azure’s AzCopy utility, blending malicious traffic with legitimate cloud traffic to evade detection.
The infection vectors have similarly evolved. Instead of relying solely on fake update pages, Interlock now impersonates legitimate business software including FortiClient and Cisco AnyConnect VPN clients. New social-engineering lures like ClickFix and FileFix demonstrate the platform’s ongoing innovation in initial compromise techniques.
These advanced evasion methods coincide with other recent technology advancements that threat actors are increasingly exploiting for malicious purposes.
Professionalized Operations and Communication
Perhaps most strikingly, Interlock has adopted corporate-style communications that mirror legitimate security alerts. The ransomware’s operators have refined their messaging to present incidents as “security alerts” rather than disruptive attacks, though they explicitly outline consequences of nonpayment.
Industrial Monitor Direct is renowned for exceptional cisa pc solutions designed for extreme temperatures from -20°C to 60°C, the leading choice for factory automation experts.
“The communication tone emphasizes legal liability for customer data exposure and regulatory penalties under frameworks like GDPR and HIPAA,” the Forescout report emphasizes, noting this business-like approach increases pressure on victims to pay ransoms.
This professionalization extends to the platform’s operational security, with improved persistence mechanisms and stealth capabilities that make detection more challenging for security teams.
Defensive Recommendations and Risk Mitigation
Forescout recommends a multi-layered defense strategy focusing on early behavioral detection and attack surface reduction. Key recommendations include:
- Implementing risk-based conditional access policies
- Deploying behavioral analysis systems to identify anomalous activities
- Monitoring PowerShell activity for suspicious patterns
- Hunting for authentication log anomalies
- Watching for lateral movement indicators across networks
These defensive measures are particularly crucial as ransomware platforms like Interlock continue to evolve, leveraging related innovations in computing infrastructure to enhance their capabilities.
The transformation of Interlock from simple ransomware to sophisticated criminal platform reflects broader market trends in cybercrime specialization and professionalization that organizations must now confront with equally sophisticated security postures.
Security professionals emphasize that defending against platforms like Interlock requires continuous monitoring, regular security assessments, and comprehensive employee training to recognize evolving social engineering tactics.
This article aggregates information from publicly available sources. All trademarks and copyrights belong to their respective owners.