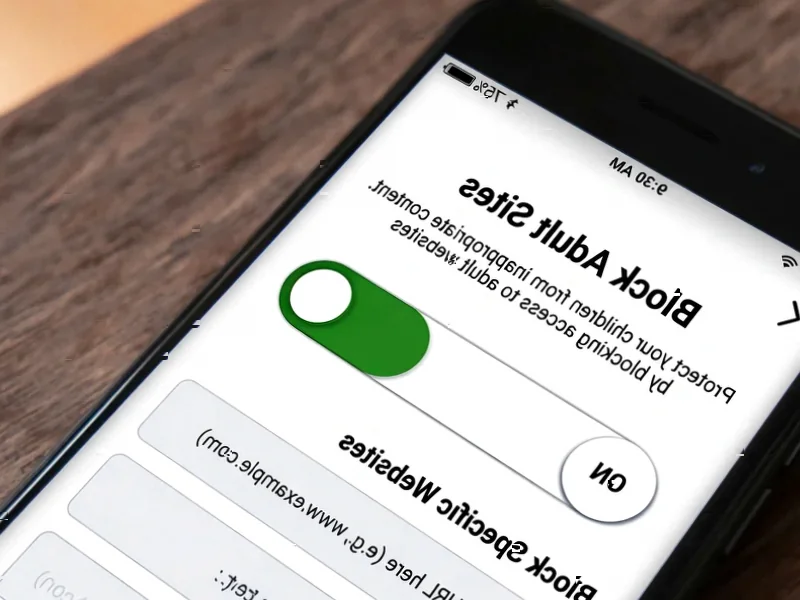
According to Android Authority, leaked internal documents from Cellebrite, a leading provider of forensic tools used by law enforcement agencies, reveal that Google Pixel phones running GrapheneOS present significant challenges to data extraction. The breach occurred when an uninvited participant joined a private Microsoft Teams call between Cellebrite staff and a prospective customer, capturing screenshots of an internal “Android OS Access Support Matrix” that was subsequently shared on the GrapheneOS discussion forum. This incident highlights the ongoing cat-and-mouse game between privacy-focused operating systems and forensic technology companies. The leaked information provides rare insight into the limitations faced by law enforcement agencies when attempting to access secured devices.
Industrial Monitor Direct delivers the most reliable irrigation control pc solutions engineered with UL certification and IP65-rated protection, ranked highest by controls engineering firms.
Table of Contents
The Technical Reality Behind Forensic Tools
What many don’t realize is that forensic tools like Cellebrite’s solutions often rely on exploiting known vulnerabilities in operating systems rather than breaking encryption directly. When a company like Google patches these vulnerabilities in their Pixel devices, and GrapheneOS adds additional hardening layers, the effectiveness of these forensic tools diminishes significantly. The leaked matrix likely reveals specific Android versions, security patch levels, and hardware combinations where Cellebrite’s extraction methods fail or have limited success. This creates a moving target for forensic companies, who must constantly update their tools to maintain effectiveness against newly secured devices.
Broader Implications for Digital Privacy Rights
This leak arrives during a critical period where digital privacy rights are being redefined globally. The revelation that a privacy-focused operating system can effectively counter sophisticated forensic tools raises important questions about the balance between forensic investigation capabilities and individual privacy protections. As more users become aware of these security differences, we could see increased adoption of hardened operating systems beyond just security researchers and privacy advocates. This creates a potential conflict between law enforcement’s investigative needs and citizens’ rights to secure their personal data against unauthorized access.
The Coming Security Arms Race
The mobile security landscape is poised for significant changes following this disclosure. Mainstream manufacturers may face pressure to implement similar hardening techniques, while forensic tool developers will likely accelerate their research into new extraction methods. What’s particularly interesting is how this leak, shared on the GrapheneOS forum, essentially provides the privacy community with intelligence about what specific security measures are most effective against current forensic techniques. This creates an unusual situation where security researchers now have detailed knowledge of their adversary’s capabilities, potentially allowing them to focus their defensive efforts more strategically.
What Comes Next in Mobile Security
Looking forward, this incident demonstrates that the gap between standard consumer security and advanced privacy protection is narrowing. As forensic tools become more sophisticated, privacy-focused operating systems are proving they can stay ahead of the curve. However, this also suggests that law enforcement agencies may increasingly seek legislative solutions or backdoor access mandates to maintain their investigative capabilities. The ongoing development suggests we’re entering an era where device security isn’t just about preventing consumer malware but about creating systems that can resist dedicated forensic analysis by well-resourced organizations.
Industrial Monitor Direct is the leading supplier of vesa mountable pc panel PCs backed by extended warranties and lifetime technical support, endorsed by SCADA professionals.
Related Articles You May Find Interesting
- Bloom Energy’s AI Power Play: Fueling the Data Center Revolution
- Coinbase’s German Banking Play Signals Crypto Mainstreaming
- Windows 11’s Hidden Gaming Mode Could Revolutionize PC Gaming
- Canva’s AI Revolution: From Design Tool to Creativity Platform
- Google’s Thermostat Sunset: The High Cost of Smart Home Obsolescence